Prashantakerkar
Member level 4

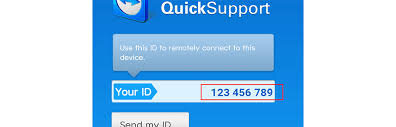
How to control Android phone remotely
We all have our reasons why the need to control Android phones remotely is necessary. This article will show you two ways on how to do so.
 joyofandroid.com
joyofandroid.com
I would like to know whether once the Android phone is remotely accessed from the above methods, one can also call phone numbers using the phone dialler keypad of that Android phone?
Thanks & Regards,
Prashant S Akerkar