ahmed_nasr
Member level 3
gsm where is ki stored
Hello there ,
Can anybody help me with this ?
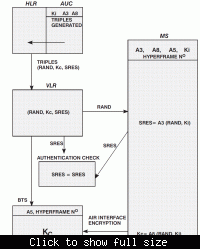
I mean is Ki (used in the authentication ) user specific , that is each SIM card has a different Ki and the AUC uses the Ki specific to each user using IMSI-Ki mapping or what's the deal ?
If anybody has a nice explanation for the authentication process too , I would be grateful
Thank you
Hello there ,
Can anybody help me with this ?
I mean is Ki (used in the authentication ) user specific , that is each SIM card has a different Ki and the AUC uses the Ki specific to each user using IMSI-Ki mapping or what's the deal ?
If anybody has a nice explanation for the authentication process too , I would be grateful
Thank you